
In a report by ThreatFabric, An Android Malware by the name of ‘Hook’ is being sold by cybercriminals who brag that it can remotely take control of smartphones in real-time using Virtual Network Computing (VNC).
For those unaware, Virtual Network Computing is a cross-platform screen-sharing system to control another computer remotely.
Moving on, the Malware is said to be promoted by the makers of Ermac; it is also an Android malware being sold at $5,000/month to the attackers, which in turn helps them to steal information from banking & crypto apps using overlaid login pages.
The malware is being distributed as a Google Chrome APK via these package names “com.lojbiwawajinu.guna”, “com.damaariwonomivi.docebi”, and “com.yecomevusaso.pisifo”.
With that being said, the creator of the malware claims that the new malware ‘Hook’ code was written from scratch, although according to the security firm, substantial codes of the two Android malware have been found that overlay each other codes with ‘Hook’ having extra features over the former.
Furthermore, the security firm mentions that the malware still contains most of the Ermac code, so thereby it is still banking malware, although there are still some useless parts found in the older strain so, which shows that the code is re-used in bulk.
In that sense, the ‘Hook,’ the android malware, is an evolved version of the Ermac and has extensive features which make it a very dangerous threat to Android users.
One of the features that the ‘Hook’ has over the Ermac is the WebSocket communication which comes in addition to HTTP traffic extensively used by Ermac. The network used is still encrypted by an AES-256-CBC hardcoded key.
Though that’s not it, the main feature of the malware is the VNC that allows the threat attackers to communicate with the interface of the infected smartphone in real-time. This enables the malware to perform anything on the compromised device ranging from Personal Identifiable Information (PII) to monetary transactions.
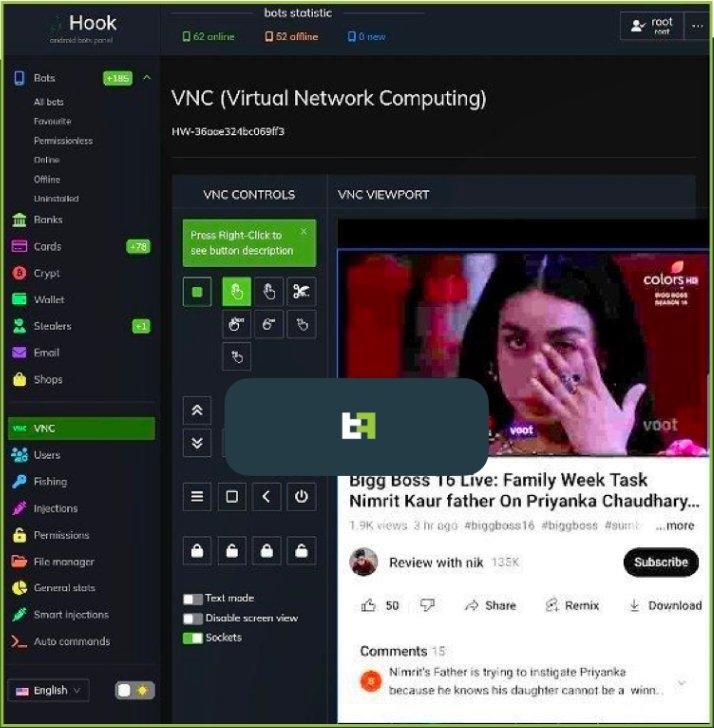
Well, the Android malware finds itself in the list of malware that is able to do a Full Data Transfer Object (FDT) and run a full chain of Fraud from the PII exfiltration to transactions with all the midway steps and without needing extra channels, said ThreatFabric.
This makes the attack difficult to detect fraud scoring mechanisms and these are new commands that the Malware can execute apart from those which are similar to Ermac.
- Start/Stop RAT.
- Execute a specific swipe gesture.
- Take a screenshot.
- Stimulate a Click at a specific text item.
- Stimulate a key press such as (Home/Back/Recent/Lock/Powerdialog.
- Unlock the device.
- Scroll up and down.
- Stimulate a long press.
- Stimulate click at a specific coordinate.
- Set the clipboard value to a UI element with a specific coordinate value.
- Stimulate click value on a UI element with a specific text value.
- Set a UI element to a specific text.
Aside from these commands, a File Manager command turns the malware into a file manager & the attackers get the record of all the files stored in the file manager and download the file of their liking.
Well, wait, there’s more; another command that the security firm found is related to Whatsapp, which allows the malware to log all the messages in Whatsapp and even allows attackers to send messages from the victim’s account.
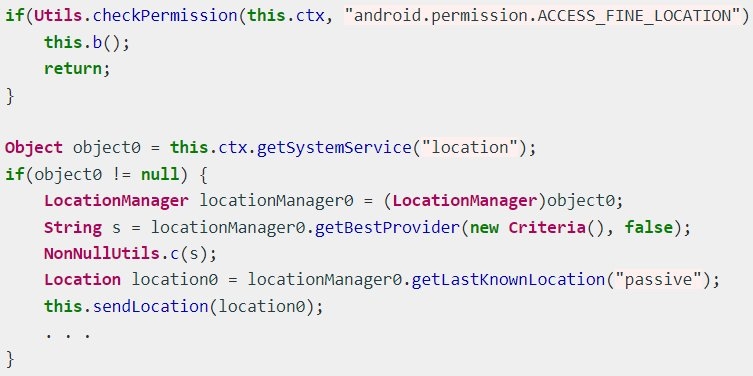
Last but not least, a geolocation tracking mechanism helps the malware to get a hold of the victim’s location by exploiting the ‘Access Fine Location’ permission.’
These are the countries in which Hook targeted banking app users – Spain, Australia, Poland, Canada, the UK, France, Italy, Turkey, Portugal, and the United States. Although one important thing to note here is that the ‘Hook’ targets worldwide.
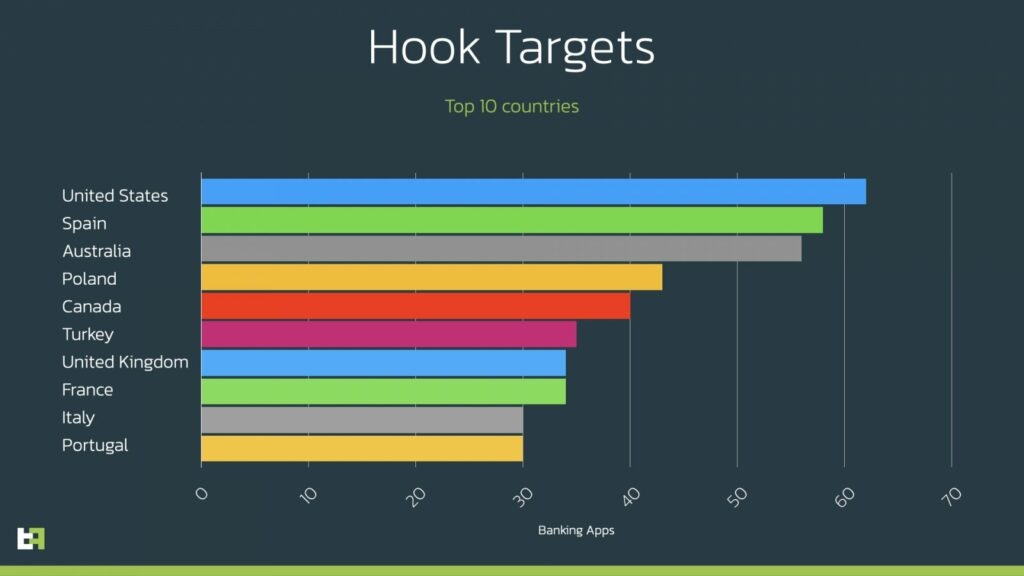
Also, ThreatFabric has listed all the apps it targets for those who are interested.
Read: Hackers Breach CircleCi’s Systems via Engineer’s Infected 2FA-Backed SSO
Directly in Your Inbox









