
In a recent development, several Signing keys used by the Android OEM to digitally sign the main system applications have been used to sign Android applications having malware.
Well, on Android, to update an app, the signing key on your phone needs to match the keys of the update that you are installing then the matching key authenticates that the update is legit coming from the OEM (Original Equipment Manufacturer) or the developer who made the app, not from some malicious source.
So the app updating procedure is not just for the apps that you download from the Google Play Store but also the bundled apps that you can update, which come from Google or the OEM. There’s already a firm set of rules or permission for the apps that you download from the play store, although the bundled apps have more access to much more powerful permissions than those on the play store.
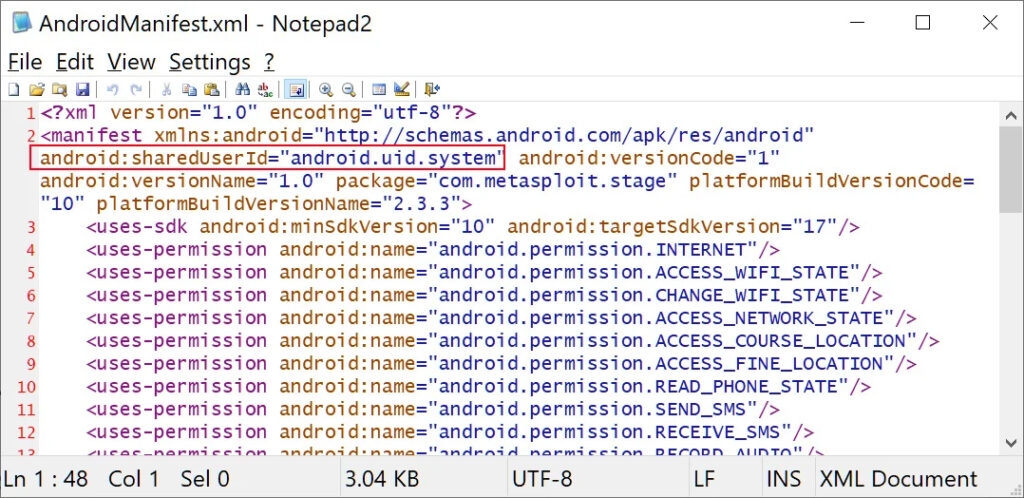
If the OEM losses or have lost their system app signing key and if the malicious apps are signed in with the same signing key, which is aligned to a highly privileged ‘android.uid.system‘ user id, then the apps will also get the system-level access to the Android device.
These privileges give access to powerful permission that is normally not given to apps, such as installing or deleting packages, managing ongoing calls, collecting information about the device, or other sensitive activities.
The abusive use of these keys was first discovered by Lukasz Siewierski, who is a Reserve Engineer on the Google Android Security team, the report which is now available on the Android Partner Vulnerability Initiative tracker.
As per the APVI, a Platform certificate is an application signing certificate used to sign Android applications on the system image. The android application runs with a high privilege ‘android.uid.system’ user id, which holds system permission which includes permission to access User data.
Furthermore, Siewierski found several signed using these ten Android platform certificates and provided the SHA256 hashes for each of the samples and digitally signed certificates.
At this time, there’s no information available about how these certificate keys were leaked to sign-in malware or if one or more threat actors have access to them, or if someone insider with authorized signed the APK with the OEM keys. Also, there’s no information about where these samples of malware were found or if they were shared on the play store or from any third-party stores.
These are ten Android platform keys packages
com.russian.signato.renewis
com. sledsdffsjkh.Search
com. android.power
com.management. propaganda
com.sec.android.musicplayer.
com.houla.quicken|
com.attd.da
com.arlo.fappx
com.metasploit .stage
com.vantage .ectronic .cornmuniif you run a search on Virustool by Google for all these hashes reveals that these platform certificates belong to Samsung, LG, MediaTek, Revoview, and Szroco.
The malware which was signed with their certificates those detected HiddenAdtrojans, information steelers, and Metasploit, and the malware droopers that the threat actors can use be used to deploy more malicious payloads on the infected device.
The search engine giant Google has issued a statement informing all the vendors which are affected and have advised them to rotate their platform keys, also to investigate what was the root cause of the leak, and retain the number of apps signed with their android platform cret to a minimum to stop the incident happening in the future.
To add to this, Google also firmly recommends minimizing the number of applications signed with the platform certificate, as it will significantly lower the cost of rotating platform keys if similar happens in the future.
To know all of the signed Android apps with possibly infected certificates, go to APK Mirror & search for them (list of the apps signed with Samsung & LG). Although Google has said that all the affected vendors have been informed of the abused platform certificates and have taken corrective measures to lower the impact on users. However, Samsung is still using the platform certificate keys that were leaked to digitally signed apps.
fortunately, these keys are just for the app updates, not the keys to sign in for OS updates, so the affected vendor can still roll out secure OTA updates that include new system apps with which they can update Google Play Protect with new keys that are compatible though that would be too much work.
Google added that they had added these infected keys to the Android Build Suite, which scans the system images & Google Play Protect also scans for the malware. Moreover, there is no evidence that this malware is or was on Google Play Store, and it recommends users make sure they are on the latest Android version.
Read: A37 Group’s Dolphin Malware Used to Steal Data & Target South Korean Paper
Directly in Your Inbox




![[Solved] "Your device isn't compatible with this version" Error on Android Android Troubleshooting](https://media.tech-latest.com/wp-content/uploads/2023/01/26144434/Android-Troubleshooting-Featured-300x169.jpg)




