
In a recent attack, a threat actor hijacked Telecom services providers and Business process outsourcing companies, diligently altering defensive mitigation that was applied when the attacks were detected.
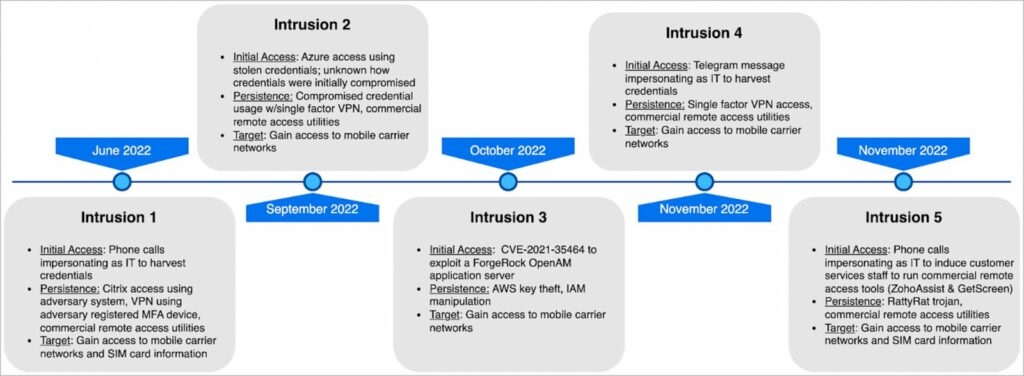
The attacks were unearthed by CrowdStrike, which mentions that these attacks have been going on since June 2022 and are still going on and the researchers have already identified five different intrusions. These attacks seem to be money driven.
CrowdStrike firm researchers who tracked these attacks aligned these to the low-confidence Scattered Spider, who shows persistence in maintaining access, altering defensive mitigation, avoiding detection, and turning to different valid targets if stooped.
Well, the security firm says the main goal of the campaigns is to break in into telecom network systems, gain access to subscribers’ information, and to conducts other activities such as swapping SIMs.
The hackers gain initial access to the cooperate telecom by applying numerous social engineering techniques, which include impersonating telecom staff, using mediums like SMS or an instant messaging app like Telegram to redirect targets to custom build phishing websites that have the company logo on them.
Well, if the company uses MFA (Multi-factor authentication), the threat attackers then deploy push notifications MFA Fatigue, which is essentially when a hacker runs scripts that attempt to log in with the stolen credentials, again and again, making it feel like endless steam of MFA push requests to the owner’s phone. Also, applying other social engineering tactics.
Read: What is a Burner Account? Is It Useful?
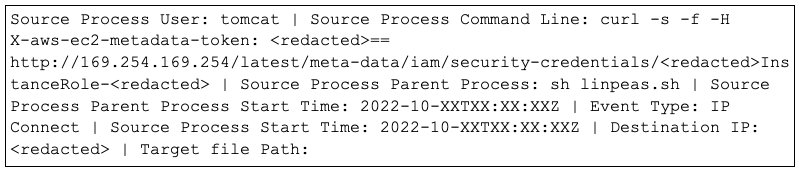
In addition to this, hackers, in one case, exploited the CVE-2021-35464 to run codes and lift their privileges using the AWS case taking advantage of the AWS case to assume or elevate privilege to Apache tomcat user, the threat actor will then request and assume permission of an instance role using an infected AWS token, mentions the security firm.
Furthermore, once the hackers gain access to the system then, they try to add their devices to the list of trusted MFA lists by using the compromised user account.
CrowdStrike also found out that the hackers are using the following remote monitoring mechanism and management tools for their campaign,
BeAnywhere
Domotz
DWservice
Fixme.it
AnyDesk
Fleetdesk.io
Itarian Endpoint Manager.
Level.io
ManageEngine
N-Able
Rport
ScreenConnect
Teamviewer
TrendMicro Basecamp
ZeroTier
Pulseway
Rsocx
Logmein
SSH RevShell and RDP Tunelling via SSH
SorillusMost of these are trusted software that corporate uses and are unlikely to give alerts on security software. Moreover, the intrusions noticed by the security firms mention that the hackers went fierce in their attempts to maintain access to the breached network even after being detected.
Moreover, in the other two observations, the threat actors seemingly got more active and deployed persistence methods such as VPN (Virtual Private Network) access or RMM tools if these mitigations were slowly applied.
In some of the other instances, the adversary went back to some of the severity methods by re-enabling the accounts which were earlier disabled by the victim organization.
CrowdStrike further added that the threat actors used various VPNs and ISPs to access the victim’s organization Google Workspace Environment and the adversaries obtained various kinds of espionage information, downloaded user lists from the compromised tenants, exploited WMI and SSH Tunneling & domain replications.
Read: A37 Group’s Dolphin Malware Used to Steal Data & Target South Korean Paper
Directly in Your Inbox









