Highlights
- A new ransomware activity, Cactus, has been exploiting a weakness. in VPN
- Ransomware exploits the weakness to gain access to the network of enterprises.
- What separates Cactus from other ransome is using encryption to protect binary.

A new ransomware activity named Cactus has been making rounds & exploiting a weakness in the Virtual Private Network (VPN) for initial access to the networks of big enterprises. The ransomware Cactus has been active since at least March and is looking to fork out huge amounts from the victims.
Now, the attackers used all the usual ransomware stuff like encryption of flies and stealing data, although the attacker added its own feel to it to escape detection. Security Reachers at the risk consulting firm Kroll think that the ransomware gets the initial access by exploiting the known weakness in Fortinet’s VPN machines.
Well, the evaluation is based on the observation that in all the events investigated, the attacker swirls inside from a VPN server VPN service account. Now what distinguishes Cactus from the other activity is the use of encryption to safeguard the ransomware binary, so the threat actors utilize a batch script to get the encryptor binary using the 7-Zip.
After that, the original 7-Zip is removed, and the binary is deployed with a particular flag that allows it to execute. The whole procedure is unusual, and as per the researchers, it is done to prevent to detection of the ransomware encryptor.
Kroll, in their technical report, the threat researchers mention that there are three ways of execution, and each one of them is selected with the use of a particular command line switch: setup (-s), read configuration (-r), and encryption (-i).
The -s and -r arguments allow the attackers to setup persistence and keep data in a C:\ProgrammeData\ntuser.dat file that is read by the encryptor when it’s running with the -r command line argument and for the file encryption to work, a unique AES key is only known to be known to the attacker must be provided via using the -i line arguments.
Read: LOBSHOT Malware Spreading via Google Ads Impersonating Authentic Remote Management Software
The key is essential to decrypt the ransomware configuration file, and the public RSA key is needed to encrypt files. As it is available as a HEX string which is hardcoded in encryptor binary, and decoding a HEX string gives a piece of encrypted data that unlocks with an AES key.
Laurie Lacono, Associate Managing Director for Cyber Risk at Kroll, said that Cactus essentially encrypts itself, making it harder to detect and helping it evade antivirus and network monitoring tools.
Running the binary with the right key for the -i encryption parameter unlocks the information and then allows the malware to search for files and start a multi-thread encryption procedure. The Cactus binary execution process is as per the selected parameters.
Furthermore, Ransomware expert Micheal Gillespie also investigated how the Cactus encrypts data and told Bleeping Computer that the malware utilizes multiple extensions for the files it targets, depending upon the processing data.
As it prepares a file for encryption, the malware changes its extension to .CTSo extension, and after the encryption, the extension becomes .CTS1. Although, as per Micheal, the malware also has a quick mode, which is a peel-to-a-light encryption pass.
Running Cactus in normal & quick mode continuously results in encrypting the same file twice and adding a new extension after every process, for example .CTS1, CTS17. According to Kroll’s observations, the number at the end of the .CTS extension varied in numerous incidents credited to Cactus malware.
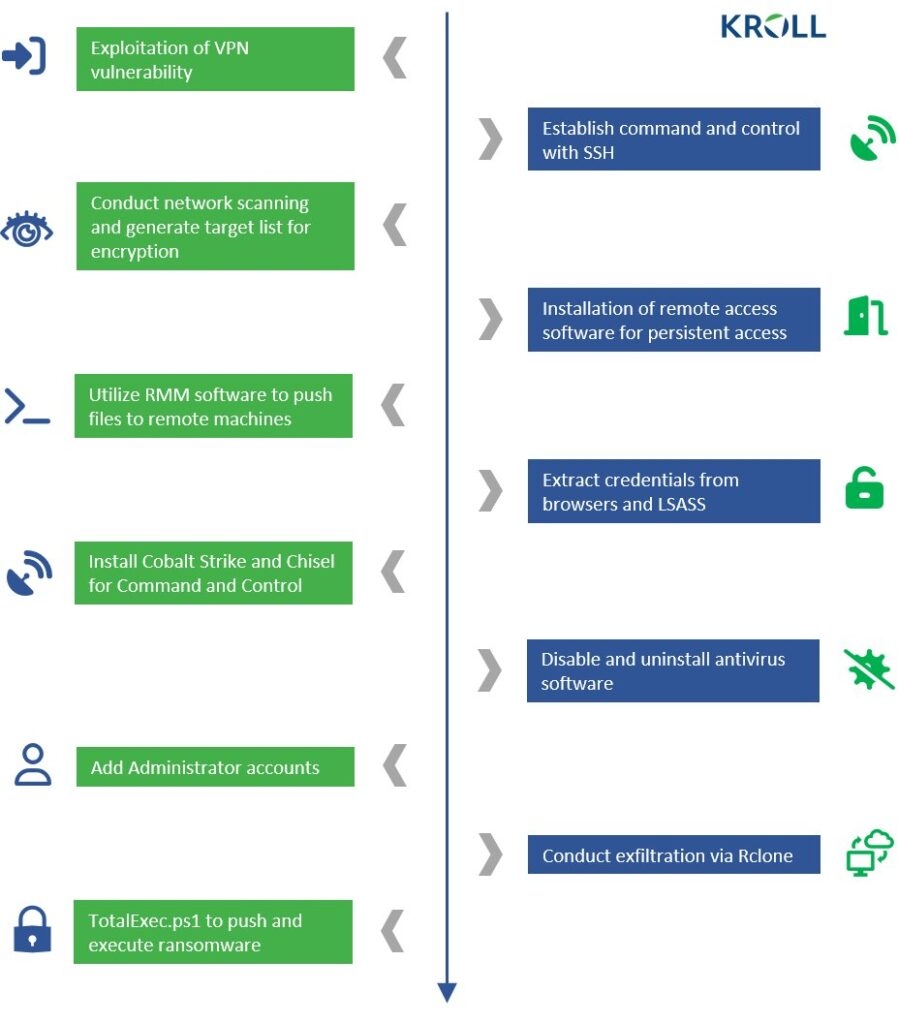
Once in the network, the threat actors used a scheduled task for persistent access using an SSH lock door which is accessible from the command and control server. According to Kroll’s investigation, Cactus depend upon the SoftPerfect Network scanner to find interesting targets on the network.
Now for deeper observation, the attacker uses a PowerShell command to list endpoints, identify user accounts by looking at successful logins in Windows Event Viewer, and ping remote hosts.
Read: Evil Extractor, Data Theft Tool Causing Havoc in US & Europe
In addition to this, security researchers also found that the malware is using a modified version of the open source Psnmp tool, which is PowerShell identical to the nmap network scanner.
Cactus tries numerous remote methods to launch various tools required for the attack through authentic tools, for instance, AnyDesk, and SuperOps RMM, alongside the Cobalt Strike and Go-based proxy tool Chisel. Researchers at Kroll say that after escalating privileges on a machine, malware operators run a batch that uninstalls the most commonly used antivirus products.
Like the majority of ransomware activities, Cactus also steals sensitive information from the victim; for this procedure, the threat actors use the Rclone tool to transfer files directly to the cloud storage.
After exfiltrating the data, the attacker used a PowerShell script called TotalExec, which frequently Black Basta attacks to automate the encryption process. Well, the encryption routine of the Cactus ransomware attacks is distinctive.
Regardless, the process does not seem to be only restricted to Cactus as a similar encryption process was also recently seen used by the BlackBasta ransomware group, told Gillespie.
Although even though the attackers steal the victim’s data but it looks like the attackers have not set up any leaked websites, which is generally the case with other ransomware activities that are involved in double extortion.
Currently, there’s no information about the ransomware that Cactus demand but as per reports, it’s in millions. The attackers threaten the victim to publish their stolen data unless they get the ransom.
Moreover, it’s clear that the attacker’s attack so far has taken advantage of the vulnerabilities in the Fortinet VPN appliance and then followed the double standard double extortion approach by stealing sensitive data before encrypting it.
Read: Phishing Scams Targeting US Taxpayers with Remote Access Malware
Directly in Your Inbox









