Highlights
- Security researchers found that the BlackCat ransomware group runs a malware-filled advertisement campaign.
- These fake advertisements lure users into fake lookalike websites of legitimate sites to download malicious software.
- Once the user clicks the download button, it downloads two files, the first is the software itself, and the second file is the malware.

Security researchers at Trend Micro discovered that the BlackCAT, also known as ALPHV, is running malware-filled advertisement activities to entice people into fake websites that look like legitimate WinSCP file transfer apps for Windows. However, putting malware-filled installers. BlackCat was found running this campaign on Google & Microsoft Bing pages.
The ransomware group is using malvertising as a lure to possibly infect the devices of IT professionals, system administrations, and web admins to get initial access to the corporate network and
Well, WinSCP is free, and an open-source SSH file transfer protocol, Amazon S3, WebDAV, and secure copy protocol client (SCP) for Windows, and the primary function of the WinSCP is to transfer files securely from the local device to the remote server.
The attacks start when the user searches for WinSCP download on either Google or Bing and then gets the promoted malicious results that are placed above the legitimate WinSCP download website.
After that, the target clicks on the malicious advertisement that takes them to the malicious website that takes them to the tutorials about carrying out automatic file transfers via the WinSCP.
Read: Threat Actors Use Trojanized Super Mario 3 Game Installer to Spread Malware
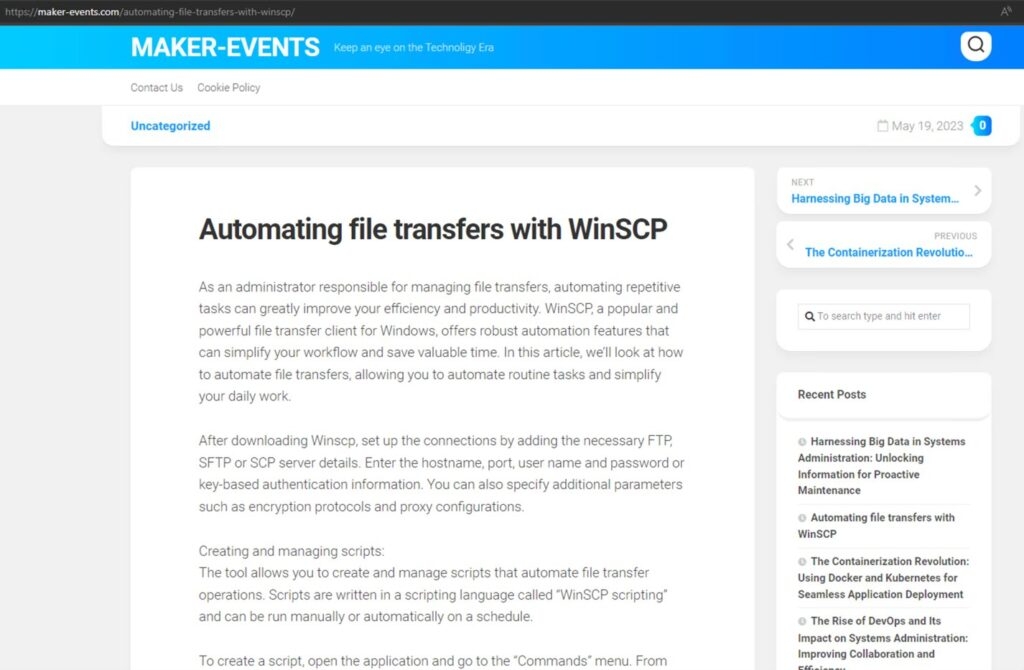
Well, these websites do not the malicious installer, possibly to escape detection of the Google & Bing Anti-abuse crawlers, instead redirecting the visitors to the fake lookalike of the legitimate WinSCP with a download button.
As usual, these fake lookalike websites have a similar domain name to the authentic winscp.net domain for the purpose, like WinSCP(dot)com.
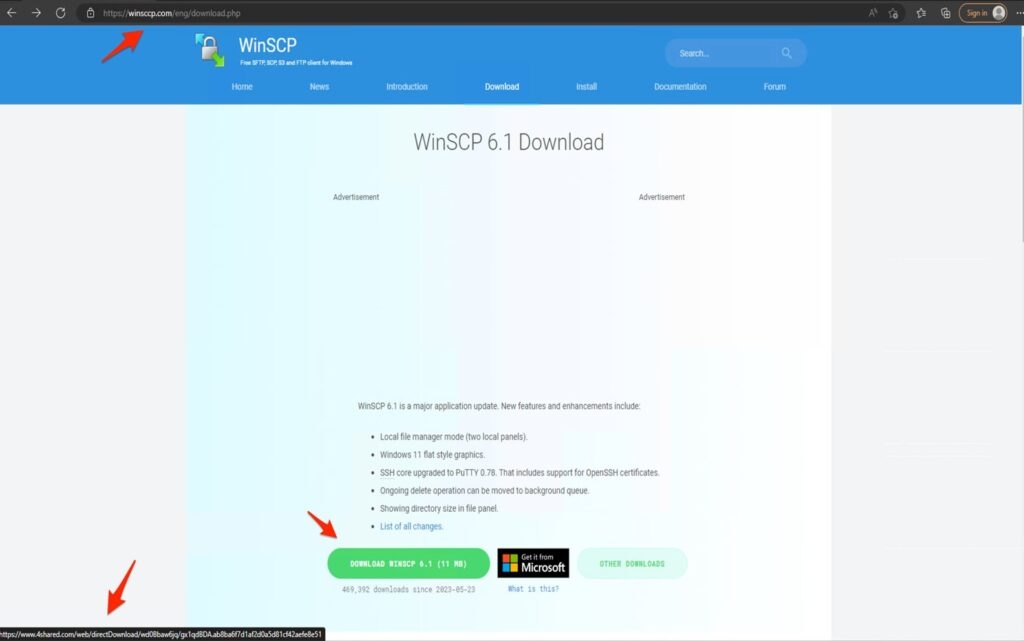
As the visitor clicks on the download button and receives the ISO file that contains “setup.exe” and msi.dlll. Now the first file is to entice the visitor into launching it, and the second file is the malware activated by the executables.
According to the cybersecurity firm, once the setup.exe is performed, it will inform the second file, i.e., msi.dll, that will extract a Python folder from the DLL RCDATA section from the legitimate installer for the file transfer app to be installed in the visitor’s Personal computer.
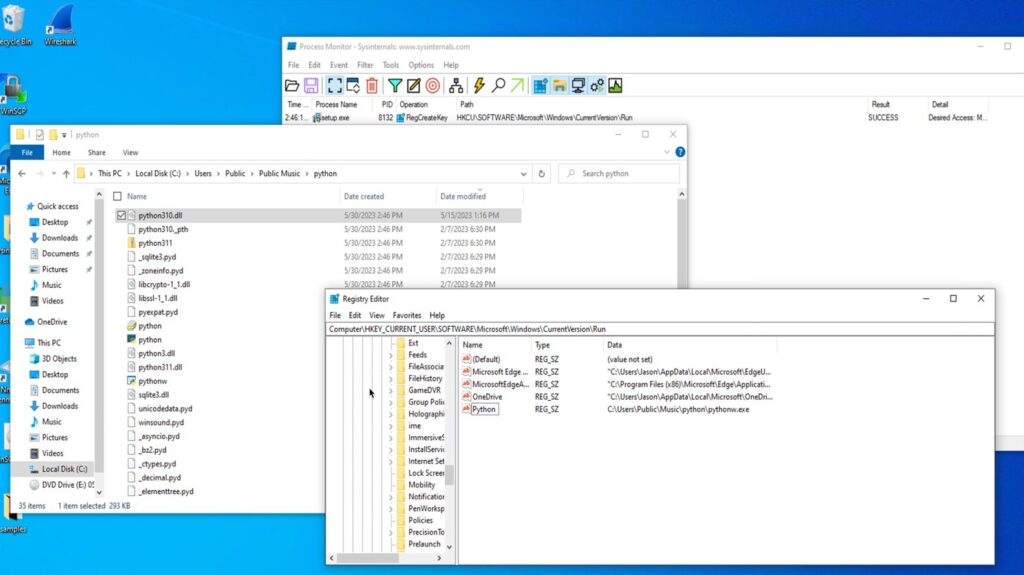
As the user performs this action, it also installs a trojan-filled python.dll and creates a persistence process by creating a run key that is Python & the value “C: \Users\Public\Music]python\phthonw.exe”.
The executable phthon.exe takes to the altered obscure python310.dll that carries a Cobalt Strike beacon that connects with the command and control server address.
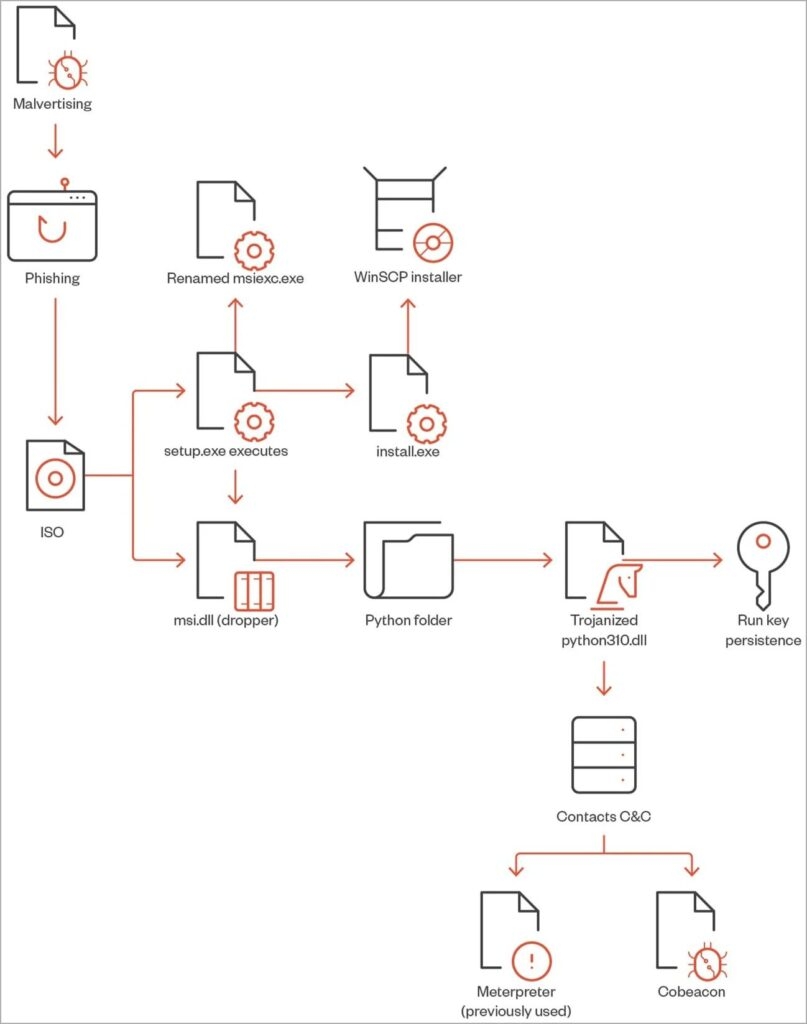
Threat actors having the Cobalt Strike running into the victim machine, it becomes easy for them to run more scripts and get the tools to move within to grow the infection.
The security firm Trend Micro observed that the threat actors are using these tools such as,
- Findstr: Command line tool used for searching passwords within XML files.
- AdFind: Command line tool that is used for retrieving Active Directory information.
- Accesschk64: This command line tool is used for user and group permission observations.
- PowerShell commands: This is used for extracting Zip files, collecting user data and executing scripts.
- Anydesk: This is a legitimate remote tool misused for continuing persistence.
- Python scripts: These are utilized for executing the LaZagne password recovery tool and getting the Veeam credentials.
- KillAV BAT: This script is used for disabling and evading detection by antivirus.
- PowerView: This script is used for Active Directory observation & enumeration.
- PsExec, Curl, and BitsAdmin: all these tools are used for the lateral movement of the infection within the network.
- PuTTY Secure Copy: This client is used for exfiltrating the gathered information from the compromised machine.
That’s not all; the threat actors, alongside all these tools, also used the SPY Termitor, an ED & an antivirus disabler that threat actors sell on Russian hacking forums.
Researchers at the security firm linked the above-mentioned TTPS infections to the Black Cat ransomware group as it also discovered a Clop ransome file in one of the C2 servers that they looked into, meaning the group could be involved in two ransomware campaigns.
Read: Massive Data Breach: Over 100K Chat GPT Accounts Stolen, Warns Group IB
Directly in Your Inbox









