Highlights
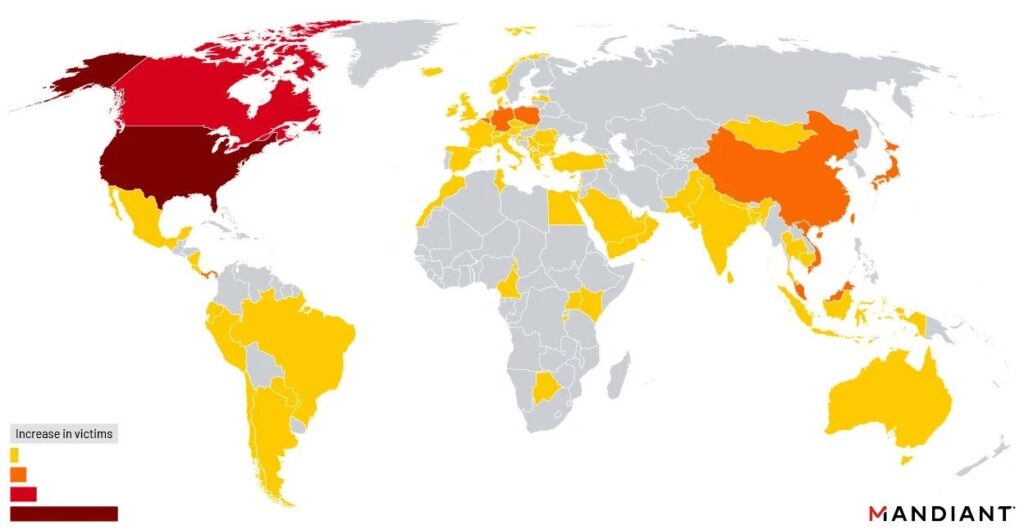
- The threat intelligence solution firm Mandiant reports that Chinese hackers excessively targeted & broke into government & government-linked organizations in recent attacks.
- Recent attacks targeted Barracuda Email Security Gateway, Zero-Day, with a specific focus on organizations all over America.
- The local government targeted in this campaign was just under 7 percent of all the identified affected organizations. However, this drastically increases to almost 17 percent when compared to the US-based targeting.

The threat intelligence solution firm Mandiant reports that Chinese hackers excessively targeted & broke into government & government-linked organizations in recent attacks that targeted Barracuda Email Security Gateway, Zero-Day vulnerability with a specific focus on organizations all over America.
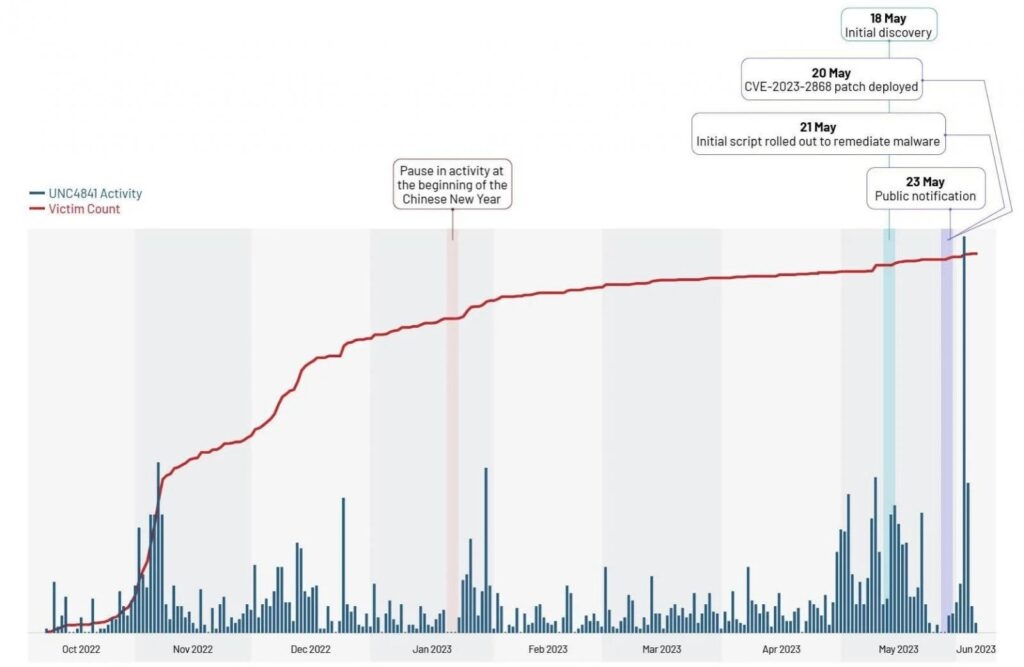
As per the intelligence firm Mandiant, nearly a third of the hacked devices belonged to government agencies, almost all of them between October & December 2022.
Notably, including North American-identified organizations, several other states, towns, provinces, tribes, cities, and town offices were targeted in this campaign.
With that being said, overall, the local government targeted in this campaign was just under 7 percent of all the identified affected organizations. However, this drastically increases to almost 17 percent when compared to the US-based targeting.
It looks like the attack’s motives were to spy as the attacker (identified as UNC4841) engaged in breaking into the system that belonged to the high authority people in the government and also the high-tech verticals.
The email security gateway informed users that the security flaw was being utilized to break into the Security Gateway devices on May 20th before Barracuda patched all the vulnerable devices remotely.
About Ten days after patching all the vulnerable devices, the company also revealed that the zero-day vulnerability had also been exploited in the attacks for at least seven months since October last year to release an unknown malware & steal data from the infected devices.
Furthermore, the company warned the customer a week later that they should replace their infected appliances immediately, including those patched, as approximately 5 percent of all the Security Gateway devices have been compromised, as per the threat intelligence firm.
Read: Instagram Deletes Fake Tim Cook Account
As mentioned above, the attacks dropped unknown malware, including the Saltwater & Seaspy, and a malicious tool named SeaSlide to get remote access to the infected devices via the reserve shells.
CISA also shared information on Submarine, also known as DeathCharge & Whirlpool malware that was dropped in the same attack as a later-stage payload to maintain control after the company advisory on the small number of infected devices belonging to what Mandiant thinks are the high-stake targets.
This indicates that although the campaign had global coverage, it was not opportunistic, and the attacker had enough planning & funds to expect and prepare for incidents that could possibly disrupt their access to the targeted network.
The threat intelligence firm’s Senior Incident Response Consultant, Austin Larsen, added that we are contending with formidable adversaries that boast vast resources, funding, and know-how to execute a global spy campaign undetected successfully. The China Nexus attackers are improving their attacks to be more impactful, stealthy, and effective.
That said, both Barracuda & Mandiant have yet to find evidence of any new Security Gateway devices infected via the CVE-2023-2868 after the flaw was patched.
In addition to this, last week, the Federal Bureau of Intelligence warned that these patches are infective as the devices are still being infected in the ongoing attacks.
The FBI also reinforced Barracuda’s warning to customers that they should separate and then replace the infected device as soon as possible, advised the company to investigate its network for possible break-ins, and urged them to change & rotate network private credentials, i.e., Active Directory to baffle the attackers attempts to maintain persistence.
Also, the federal law enforcement agency says the FBI is actively watching any intrusion and considers the Security Gateway devices to be infected and vulnerable to this exploit.
Moreover, the agency has verified that all the Barracuda-infected ESG devices, including those patched, remain at risk for continued device compromises from the suspected China threat actors utilizing the flaw.
Read: WhatsApp’s Latest Update Allows Users to Edit Photo Captions: Here’s the Scoop
Directly in Your Inbox









